
Subdomain takeovers are pretty common, as a March 2020 study of Microsoft subdomains showed. The researchers specifically found around 670 Microsoft subdomains vulnerable to hijacking.
The conundrum does not only affect large multinational companies like Microsoft, though, a subdomain takeover can affect any organization, big or small. That leads us to ask, “Is subdomain hijacking preventable?” This post looks at this question through examples, along with why subdomain lookups are probably beneficial to any firm’s cybersecurity strategies.
Subdomain Takeover Definition and Risks
Before we move on to tackle the nitty-gritty, let us first define what a subdomain takeover is.
A subdomain takeover occurs when attackers are able to seize control of a target organization’s subdomains, typically via cloud and other third-party services. It happens when web projects end but the subdomain Domain Name System (DNS) entries are not fully shut down.
Subdomain hijacking can enable threat actors to do this:
- Ask your website visitors for their account credentials
- Force your site visitors to install a malicious extension to or update their browsers and spy on them
- Ask your website visitors to upload project files
- Ask your employees to upload sensitive corporate documents
- Solicit money from your site visitors or employees
- Manipulate the content on your website and even network
- Steal administrator passwords
- Collect information about your security certificates to forge these
How Subdomain Lookups Can Help
To avoid the dangers that subdomain takeovers pose, heed the following best practices.Do a Subdomain Audit of Your Network
By creating an inventory of all your subdomains and monitoring for additions and deletions, you can better rid your network of gaping security gaps that attackers can exploit via a subdomain takeover.A subdomain lookup, for instance, using the domain name cnn[.]com turned up several hundreds results, not all of which, however, have been updated recently (i.e., in 2020 or 2021).
A total of 111 of the resulting subdomains have not been updated recently. Examples of unused subdomains include:
- One was an AT&T wireless subdomain last updated on 25 September 2017, it is no longer used
- Another was a Sports Illustrated subdomain last updated on 7 April 2014; note that Sports Illustrated changed owners in 2019

- The third is a subdomain for a blog focusing on events in the Middle East last updated on 13 May 2013; even the blog’s last post was published on 7 February 2013
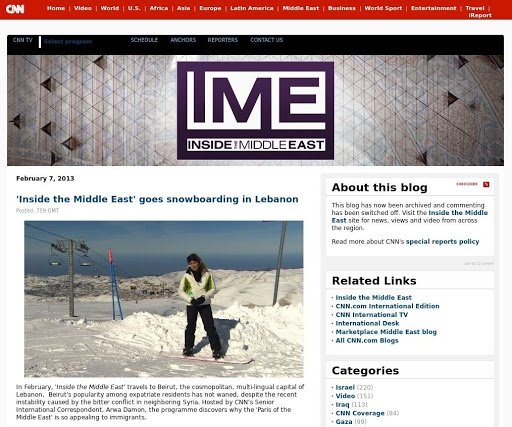
Threat actors could theoretically hijack these subdomains and use them for attacks against the news broadcaster and its viewers, partners, and employees.
See If Attackers Are Mimicking Your Web Pages
Apart from subdomain takeovers, typosquatting is another common threat to any business. Sometimes, typosquatting and subdomain hijacking go hand in hand. A study of the subdomains of 10 of the most-imitated brands today, for instance, revealed that very few subdomains that contain a company’s brand name is publicly attributable to them. That means that the majority of the subdomains do not have information about the imitated company on their WHOIS records.
Given that, performing subdomain lookups on your websites then subjecting the unknown subdomains’ WHOIS records to further scrutiny to make sure none of them are under someone else’s control would be advisable. Monitoring typosquatting data feeds to ensure no other entity is using your brand for malicious gain could improve your cybersecurity posture as well.
CNN, for instance, and other brands should look at the current WHOIS records of the subdomains found containing their names to make sure none of them are currently being used to distribute malware, spam, or phishing emails.
As this post showed, subdomain lookups can support cybersecurity strategies. First and foremost, they can help organizations ensure that none of their former or forgotten web properties could put their reputation in danger.
Posted from my blog with SteemPress : https://latesthackingnews.com/2021/01/28/why-do-subdomain-lookups-for-cybersecurity/