In part because I'm pretty open online (which exposes me to potential social engineering attacks), I'm positively paranoid about securing my devices and private information. All my computers and devices are encrypted, I use very strong passwords and don't reuse them, I use a password manager, I have enabled 2 Factor Authentication everywhere I can (preferably using the Google Authenticator app), I use an identity protection service, I have secured my cell phone carrier account with a special passcode (which is separate from my login password) so that it can't be stolen, etc., etc., etc.
So, imagine my surprise when the the following happened earlier this week:
On Tuesday, my cell phone suddenly stopped working in the middle of a call. I could not get it to reconnect to a cell tower despite that my wife's phone and my iPad, both with the same carrier, had strong signals. My phone just said "no signal" while the other devices showed 2 or 3 bars.
I attempted to solve the issue via reboots, etc. to no avail. Thinking I might have an issue with the SIM card, I put my wife's SIM into my phone and it suddenly started working again. But when I put my SIM card back in, it failed to connect. Figuring I just had a bad SIM card, I resolved to visit the cell phone store when I had some free time the following day.
The following day around lunch time (and before visiting the cell phone store), my wife (forgetting that my phone wasn't working) sent me a text message while we were a short distance apart for a few minutes. When I returned to her, she said "your response to my text was odd". I said, "what response?"
"The one you just sent", she replied.
Obviously I had not responded since my phone wasn't even working. But...terrifying, SOMEBODY HAD responded! And it looked like the response was coming from...me! This is kinda what that experience felt like for us: https://m.youtube.com/watch?v=rkcGm-pWwsQ
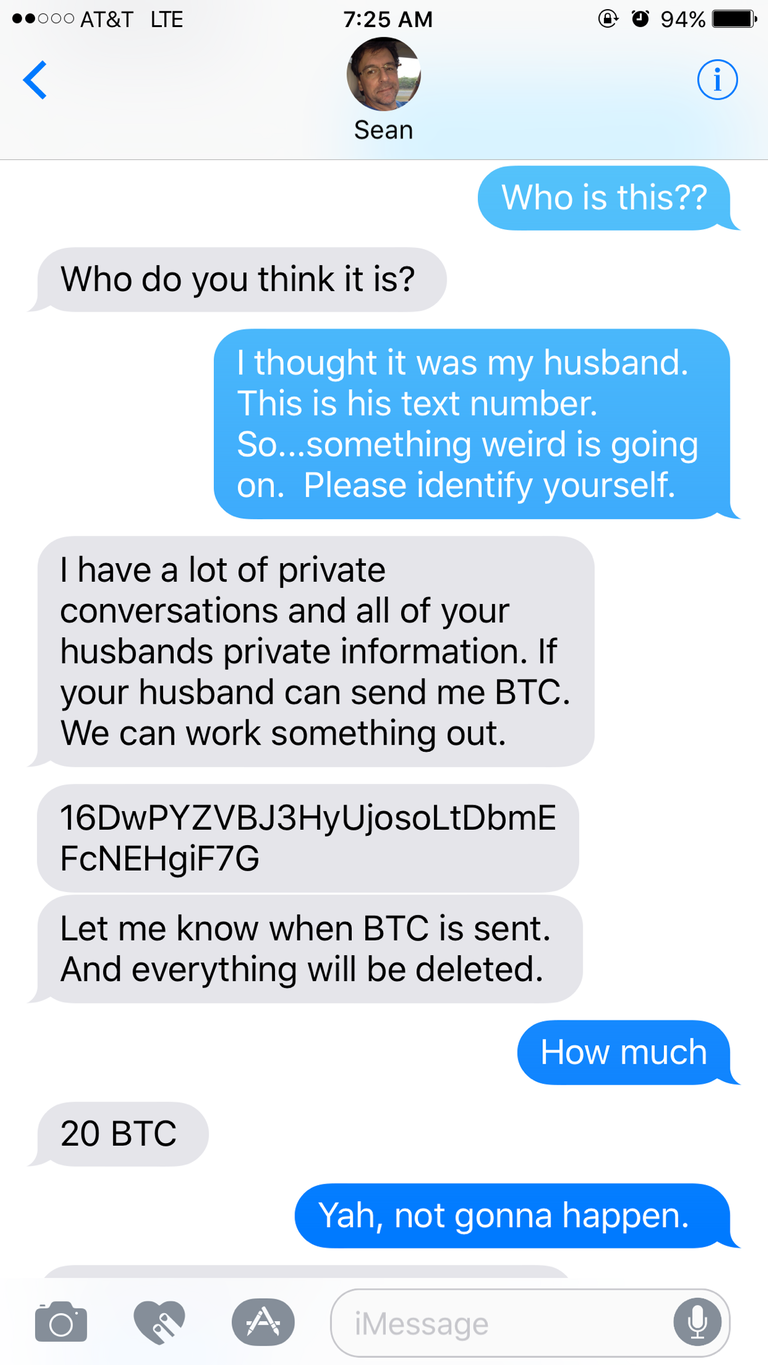
Here's part of our conversation with the hacker after we figured out we'd been hacked (my wife's portion of the conversation is in blue):
We had no intention of paying even a dime (I couldn't even if we had been so inclined), but we nonetheless played along with the hacker to gain as much information as we could and to buy time.
After some additional discussions during which the hacker tried to prove his/her bona fides--by referring to my wife by name (interestingly calling her by her legal name, Cynthia, rather than Cindy) and by texting her my social security number (which was indeed accurate)--the hacker offered to accept only 10 bitcoins rather than 20. If I would just send the coins, the hacker indicated that he/she would return my phone number and destroy all private info supposedly in his/her possession. During these conversations, the hacker also said "I have known Sean since 2011". That's an intriguing fact, if it's true.
Notice that my wife's conversation with the hacker shown above shows up in blue text, which implied to us that this was an iMessage conversation with the hacker and not SMS. That thought was terrifying! Had the hacker somehow managed to gain control over my iCloud account despite that I have a very strong password and two factor authentication enabled? Fortunately, it now appears that the answer to that question is no, though I wouldn't know that for several more hours.
While we were conversing with the hacker, we were also proceeding to the local cell phone store. Once there, I provided identification and informed the carrier agent that someone had stolen my cell phone number and was communicating with my wife via text messages in an attempt to extort money.
After checking the company's records, the agent confirmed that someone had contacted the company four times the prior day attempting to change information associated with my account and to associate my phone number with a new phone, however the agent indicated that, because my account was protected with a passcode that was unknown to the hacker, the hacker was denied and the attempt to change the account was unsuccessful.
However, obviously it was NOT unsuccessful. At this point I'm not certain whether the agent was lying to me to protect the company or whether the agent was simply mistaken, but my phone stopped working immediately after the last contact by the hacker to the cell phone company, and the hacker then began receiving all of my texts and phone calls, even impersonating me in some texts conversations. I plan to follow up with the carrier later to get to the bottom of this because its unacceptable.
Because I was able to provide ID and knew the passcode associated with my cell phone account, the agent at the cell phone company was able to replace my old nonfunctioning SIM card with a new one and then re-associated my phone number to the new card. Immediately thereafter, we lost all ability to continue texting the hacker and control over my phone number was restored to my device.
That we lost contact with the hacker immediately after our phone number was reassigned to my phone suggests that the hacker was only in control of my cell phone account for a brief time and not my iCloud account. Had he/she controlled my iCloud account, he/she could have continued to communicate with us via iMessage. I was eventually able to log into my iCloud account and change the password just to be safe, so I'm now confident that it is and was secure.
Because the hacker was in control of my phone number for about 24 hours, he/she also would have received any 2 Factor Authentication (2FA) codes sent to that phone. Were the hacker in possession of my username and passwords to my various accounts, he/she could have circumvented the 2FA security and obtained EVERYTHING. Fortunately I use strong passwords and I don't reuse passwords, and all my passwords are secured in an encrypted password manager, so it's VERY unlikely that any other of my accounts were compromised. To confirm this, I have checked the logs of my sensitive accounts and it does not appear that anyone gained unauthorized access. Just to be safe, I changed the passwords on these accounts too.
It is disturbing, however, that the hacker knew my wife's legal name and my social security number. Since it's unlikely that the hacker gained access to other sensitive accounts, how would he/she know these things? Might the hacker be someone personally known to me who would have reason to be in possession of such info (remember the hacker said that he/she had known me since 2011)? Perhaps. But anyone who knows me very well would know that my wife goes by Cindy and not Cynthia, so it can't be someone too close to me.
Regardless how can you learn from my near tragedy and protect yourself? Well, first, please know that if you happened to send me text messages between approximately 2pm eastern on Tuesday July 11th and 1:00pm eastern the following day, I did not receive those texts and the contents of such texts are now in the hacker's hands.
Second, while what I experienced was quite bad, it was, or at this stage appears to be, manageable. But it was only manageable because I had taken the necessary precautions in advance, and I STRONGLY encourage you to do the same. Specifically, please be SURE to do the following to protect yourself ASAP:
- Make sure that all of your computers and electronic devices are whole drive encrypted (most cell phones and tablets are encrypted by default, but not so with most computers.
- Use strong passwords (at least 12 digits long containing upper and lowercase letters, numbers and special symbols)
- Don't reuse your passwords across websites. Instead, use an encrypted password manager (like 1Password or LastPass) to keep track of all your login credentials.
- Enable 2 Factor Authentication (ideally using an Authenticator app rather than your phone number) everywhere you can (Facebook, Dropbox, Google/Gmail, etc.) but ESPECIALLY on any accounts that contain private or personal information and especially on the email account that you use to reset forgotten passwords.
- Secure and insure your identity against theft by using an identity protection service such as LifeLock.
- VERY IMPORTANT--Contact your cell phone provider and protect your account via a "passcode". While it was not completely successful in protecting me, it should prevent someone from impersonating you to your cell phone carrier and stealing your phone number.
That was an awesome post. I'm glad it had a happy ending.
Makes me really glad I spent the time going on a 2 week long account/data security marathon.
Things human beings can do to each other cause of money...very wicked.
yes really, totally agree with that !! thankls @sean-king for pointing out to us how vulnerable one can be and the solutions you use and suggest are certainly the correct approach i,d say !! I shall now resteem this great and important info to my followers )
Wow, interesting!, really scary, but looks like the "hacker" only was able to impersonate you and convinced the agent to give him your phone number... It cold have been anyone who knows you, dont need to know you well...
I thought about another extra precaution you could take: Dont use your public phone number to verify any account, just buy a cheap new phone and line exclusively for that, and dont give that number to anyone...
I think I read of a similar incident on Ars Technica last year and then subsequent incidents where people confirmed they had suffered the same kind of theft. It is pretty scary that the mobile phone companies can be socially engineered so easily and that they they are still open to this. Obviously their procedures for confirming identity before reassigning devices/numbers are not stringent enough. They certainly should not allow it to happen without the passcode.
Totally agree, the fact that our phones are secured by text message bothers me. I like Google Auth much better. I actually have my google auth codes backed up by winauth, in a 3 layer encrypted virtual drive only mountable by a very very long password.
I can't believe you didn't jump on to 10 BTC deal! What a bargain. It's crazy that can/did happen. It really makes you feel uneasy. I had a situation recently where someone that I did not know contacted me via Facebook Messenger. Without going into too much detail, they thought I was someone that they made a "purchase" from and they were unhappy with the "item" they purchased. An offer was made to rectify the situation if I chose and a threat was made if I chose not. The police were contacted and everything was handled but it was a creepy feeling. My Facebook profile is set to private so I don't know how he was able to message me in the first place and I also learned that it is very easy to do a quick search online and find someone's address. That part really freaked me out. It all worked out for us and I'm glad it worked out for you as well.
Thanks for posting this excellent reminder and primer on keeping your information safe. Resteeming for additional visibility.
If he was actually using that phone number, it should be possible to locate him. The police can do that, and since its a black mailing attempt you can involve them. But its too late now, I guess.
Wow...thanks for sharing
Glad it all sorted out for you. It appears more and more common. I like to think I am careful but seem not as much as I could be. Make sure you get compensation from the phone company.
I change password regularly. But I will check out how LastPass works, thanks for the tip. I am reluctant to use google authentication, I just don't trust google or like to support them, as they are to powerful and have to much information; Am I wrong with this ethos ?
Omg, those currencies...
sean-king, we need more people like you on this channel.
Btw. you can find out about yourself at this terminal, I found you based on what the machine thinks I like about you, haha.
good post.done upvoted for me.
Hackers... Even if you protect yourself as much as possible, they find some ways to hack something. It's good to hear that you didn't really lose anything from this hacking attempt.
Yes security always first thanks for post and alert!
Holy balls that's just insane! Lol 20 BTC they're having a laugh...
Seeing those screenshots of your wife talking to this hacker blows my mind. Scary stuff.
Its good that you share your experience..... now are aware of these kind of cases...
Now a days money is more important then human beings....... very bad .
the desperation in a man's mind... wooo! thanks for sharing this post @sean-king
Thanks for this vital information. Precaution is better than cure, Thank God you have taken precaution already
Great advice! Part of the trouble with being "too" connected today is the work involved in keeping your ID/data safe. I'm not sure I'd like all that encryption in my life so that's why I store my two $100 bills in my mattress!
Thanks for sharing your story and tips to protect yourself! I resteemed this one for spreading the word! Great post!
Wonder how they got that social security #? Any documents in the phone that would have it? It sounds like a amateur who just tricked the phone company rather than a pro to me. 20 BTC is an outrageous demand, even 10.
Agreed on all counts. Not sure how he got my SSN though. I'm sure the cell phone company has it, so perhaps he connned it out of them somehow.
Scary stuff. With (I assume many of us here) having so many of our assets in Steem Power, we have to be very careful, even though there is a power down delay.
Glad you got things sorted out and no real harm was done. I would lodge a complaint with your cell provider, they fucked up somehow and owe you a discount/explanation.
Scary Times, that is so disturbing, I would be creeped out!!
Thank You for the tips! never know when this can happen!