On Aug 28-29, 2018 the Five Eyes nations of Australia, Canada, New Zealand, the United Kingdom, and the United States met in Australia to discuss next steps in securing deeper access to online encrypted data. Assuring that their intention is to protect their citizens, they argue in favor of gaining the cooperation of stakeholders in the technology industries to assist with 'lawful' access to the private data they already are in possession of through the NSA. They are asking for backdoor access to end-to-end encrypted private data. Quite telling is the following statement in the Five Eyes "Statement of Principles on Access to Evidence and Encryption".

"The increasing gap between the ability of law enforcement to lawfully access data and their ability to acquire and use the content of that data is a pressing international concern that requires urgent, sustained attention and informed discussion on the complexity of the issues and interests at stake. Otherwise, court decisions about legitimate access to data are increasingly rendered meaningless, threatening to undermine the systems of justice established in our democratic nations."
https://www.homeaffairs.gov.au/about/national-security/five-country-ministerial-2018/access-evidence-encryption
The 'gap' between 'ability to acquire and use' and the 'ability of law enforcement to lawfully access' data seems to be what has the Five Eyes in a tithy. It's encryption that prevents them from reading the data as it passes through their many and various surveillance systems.
"The Governments of the Five Eyes encourage information and communications technology service providers to voluntarily establish lawful access solutions to their products and services that they create or operate in our countries. Governments should not favor a particular technology; instead, providers may create customized solutions, tailored to their individual system architectures that are capable of meeting lawful access requirements. Such solutions can be a constructive approach to current challenges."
https://www.homeaffairs.gov.au/about/national-security/five-country-ministerial-2018/access-evidence-encryption
And here we see the ultimatum: either voluntarily come up with access solutions so the Five Eyes can read encrypted private data, or they will use legislation 'or other measures' to make tech companies comply with the latest Five Eyes demands to invade the privacy of citizens, under the thinly disguised claim that such enables protection and safety of citizens.
"Should governments continue to encounter impediments to lawful access to information necessary to aid the protection of the citizens of our countries, we may pursue technological, enforcement, legislative or other measures to achieve lawful access solutions."
https://www.homeaffairs.gov.au/about/national-security/five-country-ministerial-2018/access-evidence-encryption
Whether the Five Eyes nations realize it or not, their disclosure of helplessness and reliance on the cooperation of the technology industries speaks volumes about their incompetency, both in technology and in law enforcement. The fact of the matter is, with the level of access to private information they already have, they have not managed to come to grips with crime. This is not for lack of data nor laws, but for lack of law enforcement. They possess both intelligence information and the laws to act upon criminal activities. But they don't act on crime. Too often, local forces are told to 'stand down' and let the CIA/FBI handle it, but they don't. Rather, they cover up criminal activity. So, is the request of Five Eyes for MORE data even genuine? Likely not.
In fact, the incidents reported in the FBI's Internet Crimes Complaint Center (IC3) reveal that online terrorism and hacktivist incidents are the LEAST prevalent of all online crimes and that, despite the Five Eyes stated concern for the same.
"Cyber security and resilience of critical infrastructure
The increasingly digitised and networked nature of all aspects of our economies and societies means that cyber security and resilience is of the highest priority. The cyber domain is a vector for threats posed by hostile state actors, criminals, terrorist networks and hacktivists. A cyber attack is an attack on our communities and our sovereignty. We affirmed our collective resolve to deter malicious cyber activity, including improving domestic resilience, and coordinating technical attribution and operational response policies to mitigate significant cyber incidents. We agreed to further strengthen connectivity between our cyber watch offices to enhance shared 24/7 monitoring of hostile cyber activity."
https://www.homeaffairs.gov.au/about/national-security/five-country-ministerial-2018/access-evidence-encryption
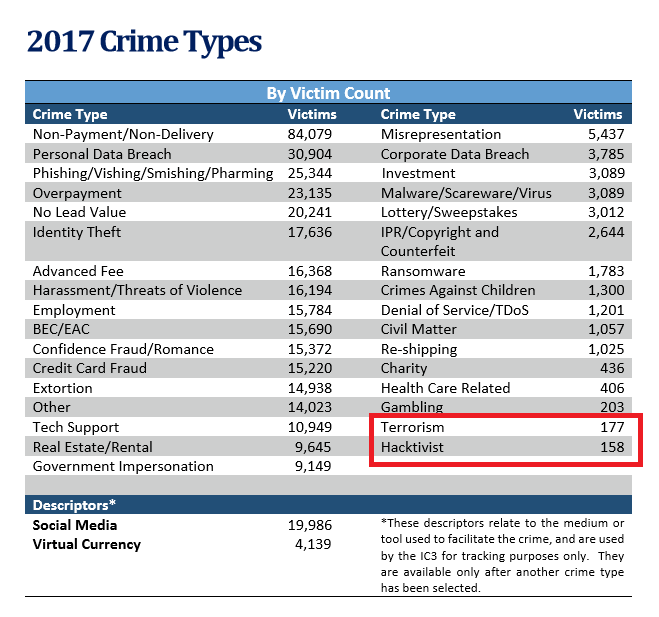
Source: Page 20 of the FBI's 2017 Internet Crime Report
https://pdf.ic3.gov/2017_IC3Report.pdf
The "hostile state actors, criminals, terrorist networks and hacktivists" that the Five Eyes claim they see operating in CyberSpace, are nearly non-existent, according to the FBI's own account. Neither the premise, nor the proposal of the Five Eyes is competent or well-intended to protect and secure public interest. Look at the FBI report. Do you see what has become a significant threat to citizens?
Personal Data Breach (30,904), Identity Theft (17,636) and Tech Support Fraud (10,949), all of which are enabled by the existing backdoor access that Five Eyes agents insisted be incorporated into social media platforms and device operating systems.
Below is a segment of a script I intercepted as it harvested my data from G+ in March 2017. Notice the warning highlighted at the bottom and the code copyright at the top. This script was written by MIT and they and Google are responsible for allowing it to leak, enabling hackers to impersonate users and steal information.
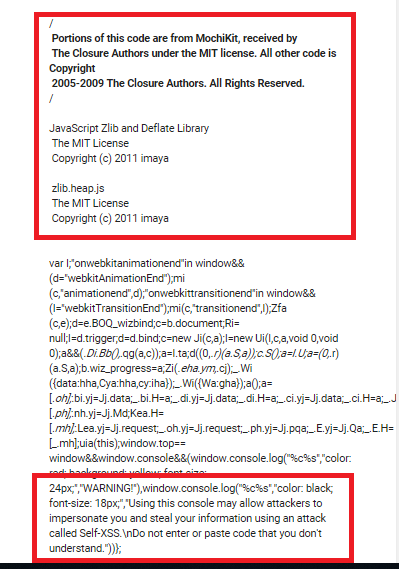
Now, you have to ask why MIT wrote the script in the first place, don't you? And I have to wonder if it was MIT running the script that hacked my data. Why? Because just prior to this incident I received a call from MIT, which I confirmed by calling the 'wrong number' caller back and finding the actual origin of the number through my phone record. 1-781-981-9275 links to MIT Lincoln Lab, 244 Wood St. Lexington, MA. This is the facility located near Hanscom AFB, which provides Homeland Protection R&D for the government. Hacking our computers and social media profiles is part of "Homeland Protection", apparently.
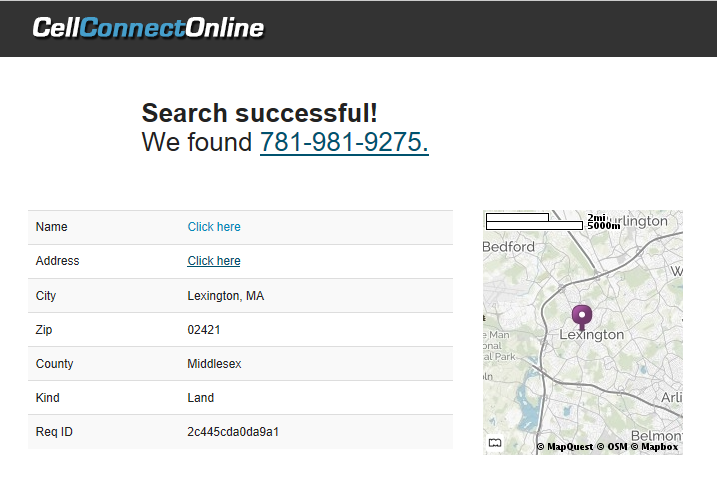
Source: http://www.cellconnectonline.com/successful.php?v=781-981-9275
Compare the location of the Verizon landline phone number in the map above with the Google map of the zip code below. Zoom to MIT Lincoln Lab on the northwest corner of the zip code boundary.
Map of Lexington, MA 02421 Zip code with MIT Lincoln Lab to the northwest within the zip code boundary.
https://goo.gl/maps/RMYUuR6WG8B2
MIT Lincoln Lab Contact Page - The number isn't an exact match. The extension differs.
https://www.ll.mit.edu/contact-us
I wouldn't expect they'd call from a public number. When I called the number back, I got an answering machine, but no details about the agency. Just, "Leave a message after the tone..."
This incident in early Mar of 2017 coincided with the release of Vault 7 from WikiLeaks. I had been reporting on it at the time and finding much more than the DOD/CIA/NSA likely wanted revealed.
Edward Snowden tweeted evidence that the USG was "secretly paying to keep US software unsafe". The evidence I have of being hacked certainly confirms that the backdoor access scripts were indeed out of the control of the government and into the hands of hackers, OR it is the GOVERNMENT DOING THE HACKING.
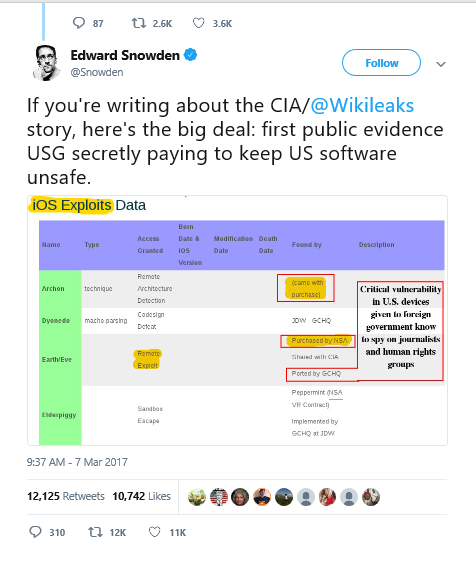
I'm inclined to think it's the latter and when Five Eyes demands more data, we can all be quite certain it is NOT to protect the interests or safety of citizens. Quite the contrary. Quite the contrary!
Related articles:
'Five Eyes' governments call on tech giants to build encryption backdoors -- or else
Zack Whittaker
or
https://techcrunch.com/2018/09/03/five-eyes-governments-call-on-tech-giants-to-build-encryption-backdoors-or-else/
https://www.technocracy.news/five-eyes-governments-demand-back-door-access-to-social-media-data/
Five Country Ministerial 2018
https://www.homeaffairs.gov.au/about/national-security/five-country-ministerial-2018
Statement of Principles on Access to Evidence and Encryption
https://www.homeaffairs.gov.au/about/national-security/five-country-ministerial-2018/access-evidence-encryption
Five Eyes Puts Pressure on Tech Giants to Lessen Protection – Scholar
https://sputniknews.com/us/201809061067813846-five-eyes-tech-gov-protection/
Tech Giants Testify to Congress as ‘Five Eyes’ Demands Access to Encrypted Data
https://sputniknews.com/analysis/201809061067788594-tech-giants-testify-congress-encrypted-data/
Bureau of Justice Statistics - Cyber Crime
https://www.bjs.gov/index.cfm?ty=tp&tid=41
FBI Cyber Crime
https://www.fbi.gov/investigate/cyber
FBI Internet Crime Complaint Center (IC3) Reports
https://www.ic3.gov/media/annualreports.aspx
FBI Internet Crime Complaint Center (IC3) Report 2017
https://pdf.ic3.gov/2017_IC3Report.pdf


Curated for #informationwar (by @wakeupnd)
Our purpose is to encourage posts discussing Information War, Propaganda, Disinformation and other false narratives. We currently have over 10,000 Steem Power and 20+ people following the curation trail to support our mission.
Join our discord and chat with 250+ fellow Informationwar Activists.
Join our brand new reddit! and start sharing your Steemit posts directly to The_IW, via the share button on your Steemit post!!!
Connect with fellow Informationwar writers in our Roll Call! InformationWar - Leadership/Contributing Writers/Supporters: Roll Call
Ways you can help the @informationwar
I upvoted your post.
Best regards,
@Council
Posted using https://Steeming.com condenser site.
Thank you, Council and Yehey! I followed and upvoted one of your posts.
Recent related articles
Older related articles
Please write an article with #interesteem tag.Interesteem(@interesteem) is a service that recommends related articles using DeepLearning.