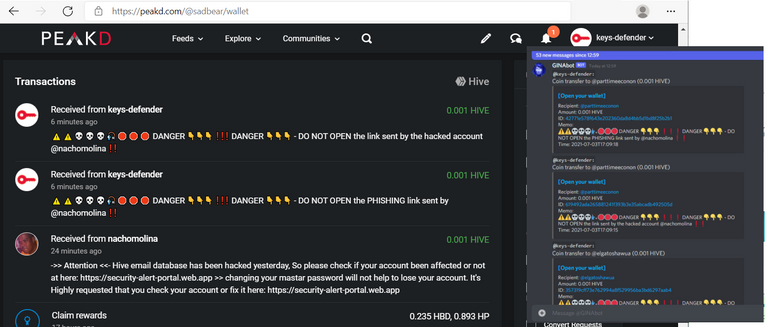

It looks like the usual phisher that has been plaguing Hive for months is still using the hacked account with high reputation @nachomolina to spread phishing.
Since he was not successful spamming phishing links through comments, he now started sending out waves of phishing memos into your wallet. WATCH OUT!
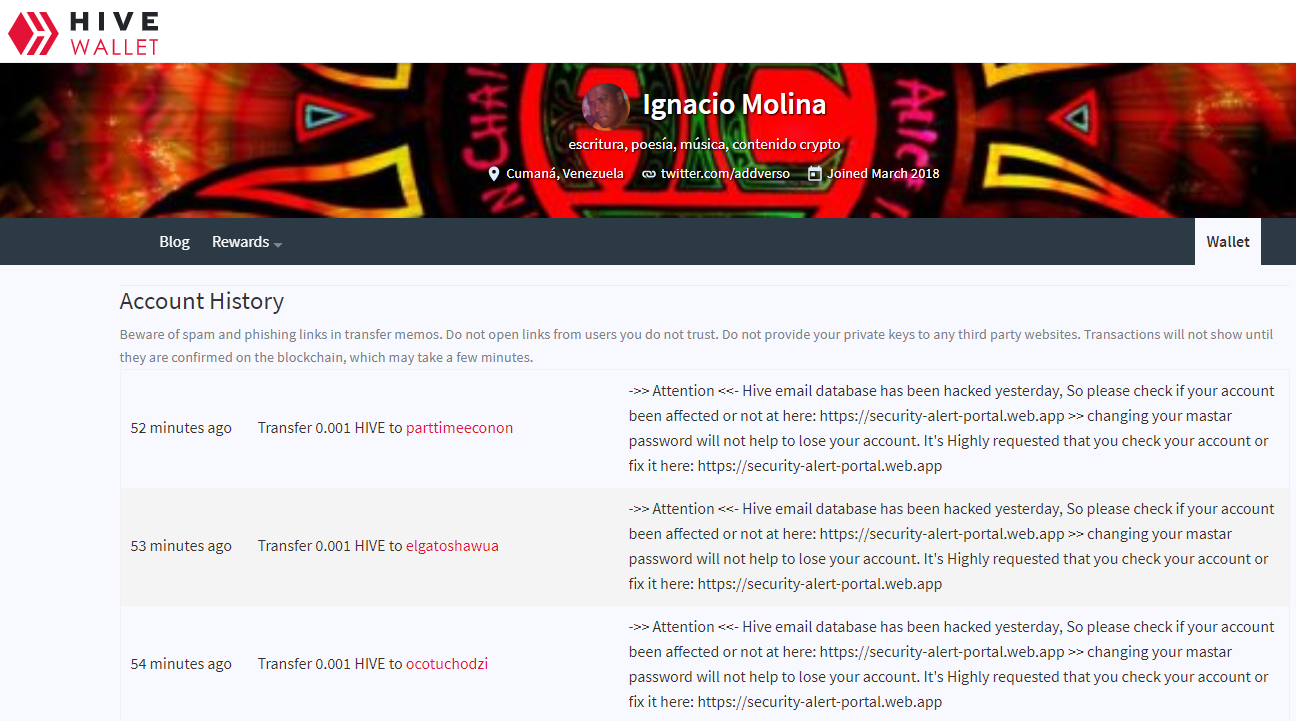
There was not a Hive database hack (of course, hive is decentralized).. it's just phishing!
(after a delay caused by a [now fixed] bug) has been automatically replying to all users that received such phishing memos.@keys-defender
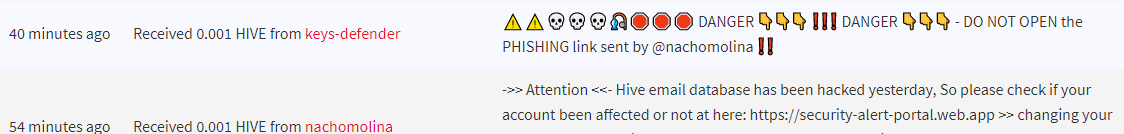
The memo-autoreply occurs automatically for any phishing link that gets reported using my !PHISHING command (eg. "@keys-defender !PHISHING https://free-hive-of-course.com").
Furthermore, thanks to the newly introduced "moonwalk scan" improvement, older memos (and comments) in previous blocks will also be auto-responded to soon after a new phishing link is reported. So keep doing your part and report anything suspicious!
Take care and keep your private keys safe!
@keys-defender
- XSS vulnerabilities in #########.com
- XSS vulnerabilities in hive-db.com
- XSS vulnerabilities in scribe.hivekings.com
- XSS vulnerabilities in hiveblockexplorer.com
- Malicious ads redirecting all Steemit iOS users to a phishing site
- Reverse tabnabbing and clickjacking in steem.chat and steeemit registration page
Other contributions:
- Universal script to prevent phishing in all Hive frontends
- Commands for community reports and ban/mute lists
Future development: plan
Keys-Defender features:
- Phishing protection [live scan of comments and posts to warn users against known phishing campaigns and compromised domains or accounts, scan of memos and auto-replies, anti phishing countermeasures - eg. fake credentials]
- Re-posting detection [mitigates the issue of re-posters]
- Code injection detection [live scan of blocks for malicious code targeting dapps of the Hive ecosystem]
- Anti abuse efforts [counteracts spam from hive haters and milking campaigns]
To support this project..

UPDATE 06/07/21 00:50
About 1 hour ago the phisher went full-blast on steem
New link now blacklisted in case he starts spreading it on Hive too.
UPDATE: (07/07 9pm)
Old blocks now being scanned in parallel with new blocks added to the Hive blockchain.
the attacker must have tested a phishing link and once figure out that it did not receive my auto-reply (@keys-defender was temporarily down due to a connectivity issue) it went full blast on hive too with this new PHISHING message: https://peakd.com/hive-150329/@rentmoney/warning-scam-alert-keep-your-keys-safe-video-inside
UPDATE: (08/07)
New phishing wave being counteracted and targeting Leo users again.

The thing that bothers me the most about this, is how awful that lie is. What the fuck is a "Hive Email Database" even supposed to be? Even if there was one, why would that put an account's keys at risk? How many people signed up with an email anyways? Of those people, why would they think their key is attached to it?
<p dir="auto">Unfortunately, I know some people may still fall for this, but god damn I hate when scams seem to not even try. For instance, their whole scam is just a ploy to get you to enter your private key into a fake HiveSigner page: <p dir="auto"><img src="https://images.hive.blog/768x0/https://files.peakd.com/file/peakd-hive/chimp.ceo/23twAQD1x898Sdit9zQ3F42xNLHwNE2poHv5b69gN3duCtsh38GvGYHgvqne7gn2VTMAk.png" alt="image.png" srcset="https://images.hive.blog/768x0/https://files.peakd.com/file/peakd-hive/chimp.ceo/23twAQD1x898Sdit9zQ3F42xNLHwNE2poHv5b69gN3duCtsh38GvGYHgvqne7gn2VTMAk.png 1x, https://images.hive.blog/1536x0/https://files.peakd.com/file/peakd-hive/chimp.ceo/23twAQD1x898Sdit9zQ3F42xNLHwNE2poHv5b69gN3duCtsh38GvGYHgvqne7gn2VTMAk.png 2x" /> <p dir="auto">Look legit, right? (<em>well, expect for that domain, which by the way hosts a fake steemconnect app on it's main page) Here's where their lack of efforts reveal themselves. Click on any of those links in the footer (<em>Apps, Accounts, etc.), and you'll see the scammers didn't even bother implementing something for them: <p dir="auto"><img src="https://images.hive.blog/768x0/https://files.peakd.com/file/peakd-hive/chimp.ceo/23tSuc4yYgKz9hBJr1ue1542paKX4fcMx4RVS73JVMS1Sm4eKZBtDvDk79ALkTcsXWa67.png" alt="image.png" srcset="https://images.hive.blog/768x0/https://files.peakd.com/file/peakd-hive/chimp.ceo/23tSuc4yYgKz9hBJr1ue1542paKX4fcMx4RVS73JVMS1Sm4eKZBtDvDk79ALkTcsXWa67.png 1x, https://images.hive.blog/1536x0/https://files.peakd.com/file/peakd-hive/chimp.ceo/23tSuc4yYgKz9hBJr1ue1542paKX4fcMx4RVS73JVMS1Sm4eKZBtDvDk79ALkTcsXWa67.png 2x" /> <p dir="auto">It's truly bottom of the barrel effort here, and even then it's still so pathetic. <p dir="auto">By the way, when you enter a key into that fake HiveSigner app, for those curious, it submits your username & key to the scammers database, so they can harvest them & presumably lock you out of your account before draining all of the funds, and then responds with:<br /> <code>{"msg":"success","url":"https:\/\/justnetwork.tech\/hiauthme\/thank-you.php"} <p dir="auto">Which basically just ends up redirecting your browser to show this: <p dir="auto"><img src="https://images.hive.blog/768x0/https://files.peakd.com/file/peakd-hive/chimp.ceo/23tcQixRoZaEj7HizdP1aDrxHiFxfXRyo6Prkg3uMmxNrp9TZWdzq9mPmek6w8nTVX3tY.png" alt="image.png" srcset="https://images.hive.blog/768x0/https://files.peakd.com/file/peakd-hive/chimp.ceo/23tcQixRoZaEj7HizdP1aDrxHiFxfXRyo6Prkg3uMmxNrp9TZWdzq9mPmek6w8nTVX3tY.png 1x, https://images.hive.blog/1536x0/https://files.peakd.com/file/peakd-hive/chimp.ceo/23tcQixRoZaEj7HizdP1aDrxHiFxfXRyo6Prkg3uMmxNrp9TZWdzq9mPmek6w8nTVX3tY.png 2x" /> <p dir="auto">No actual account -> key verification checking... So... I'm not <em>saying you should flood their fake HiveSigner app with a bunch of fake username + key combinations... I'm just saying <em>if one were to write a script that just submits fake data every second & runs in non-stop... Technically, it would be very hard for the scammers to wade through the bullshit data to find the real data. Unless they wrote a script themselves to auto try all the data they get... Which would mean we'd want several good guys to run the fake-data script all day every day... Anyways, I'm just pointing out the obvious here, and <em>totally not suggesting anything... <hr /> <p dir="auto"><strong>Thanks for you work in fighting this.I do run it every time and noticed that when I do their next attack starts later because they spent more time trying the thousands of credentials (script, multiple people manually? Not sure).
In other attacks they were trying to collect people’s username and passwords to do credentials stuffing into their email provider. I suspect that’s how they found a private key of a user that unfortunately lost 200 k 😌
Right, I forgot about the sign up emails. I created my accounts through code and paying 3 HIVE :)
1 - https://hive.blog/@keys-defender/watch-out-new-phishing-wave-do-not-vote-for-leofinance-using-that-link-its-phishing 2 - https://hive.blog/@keys-defender/new-phishing-wave-do-not-fall-for-it-there-is-no-mainnet-launch 3 - https://hive.blog/@keys-defender/there-is-no-airdrop-it-s-just-phishing 4 - https://hive.blog/@keys-defender/phishing-campaign-on-hive-be-aware
I’ll tell you more (since this is not sensitive anymore). A few months back their profile ID leaked into their phishing page code so I was able to programmatically poll that profile every 30s to found out immediately when they published a new phishing site. That way multiple times their attack stopped immediacy because they were already discovered. I must have driven them crazy because eventually they stopped (or at least for a couple of months - until now that they started using a different hosting provider).
There is also great work by other people like @guiltyparties and @louis88 that immediately contact the hosting services to take the phishing site down!
We are collecting more intel on them as they keep making mistakes. Stay tuned 😉
Ah, I see you're way ahead of me on that one 😅
<p dir="auto">Yeah, I noticed this recent domain is being hosted on <code>web.app which I believe is a Google hosting service, so hopefully it'll be easy to send in phishing reports. <p dir="auto">Again, great work fighting against these attacks. Cheers! 🍻Thanks, and thank you for the delegation as well! =]
Thanks for what you are doing, you helped me to avoid this scam on a post a while back. I probably wouldn't have fallen for it, but who knows. Keep up the good work :-)
I think @peakd and other front ends should allow hiding all messages as default. This helps newcomers a lot IMO.
Because how many are really useful for average?
Yeah, I agree
Thank you for getting the word out. I love fish but I do not care much for phishers.
Image above borrowed from technologyforyou.org ↗
Posted Using LeoFinance Beta
I’m gonna steal one from @nonameslefttouse…Your comment made me imagine if fish is good on !PIZZA! 😁😅
$PIZZA@sgt-dan! I sent you a slice of on behalf of @savvyplayer.
Learn more about $PIZZA Token at hive.pizza (1/10)
Thanks for the job you do exposing these bastards.
Posted Using LeoFinance Beta
Appreciate the info. my stuff seems fine .
What do you mean? How did you check??
I hope that you did NOT use the link you received in your wallet that invited to do so on their phishing website.
As usual I am submitting into the phishing site thousands of fake private keys so that should give us some time but If that’s the case, reset your keys immediately!
Oh no I know there's nothing in my wallet it's the same as it was a month ago. There's no links and then you're talking about below the wallet of course I'm going to ignore those 100%
Good
We appreciate your efforts to recognize those links.
Doing my best to improve @keys-defender when I have time. Slow and steady wins the race.
The truth
they are exploring new ways to do that. This is really bad I hope no one has used their link.
thanks for the information
thanks, have a great day and weekend 🙏
Yeh hopefully they’ll read my memo on top first.
Thanks, you too.
Thanks so much for this reminder.
Thanks for the advice!
Thanks for such an important info will definitely be avoiding such link.
Your post was promoted by @jfang003
Thanks for all you do.
!BEER
View or trade
BEER.!PHISHING https://moonwalk/071421-a?bottom=55638100&top=55645000
Parameterized moonwalk started!